Exchange 2010 Web Access Architecture
A detailed diagram of the Exchange 2010 architecture is available here. However, for this article a working knowledge of Microsoft IIS and Apache are assumed. Exchange uses one or more Client Access Servers (CAS) to allow client Access to information maintained in Mailbox Stores. The CAS is integrated with Active Directory, IIS and Exchange MAPI (among other protocols) to authenticate and present information to a variety of clients such as Outlook, POP3 / IMAP4 programs and mobile devices. Access to scheduling information is provided through ActiveSync.
In older versions of Exchange, the Outlook Web Access (OWA) server was simply an IIS server that could be placed in the DMZ for security. Exchange 2010 CAS servers, being closely integrated with Active Directory, require almost unrestricted access to Domain Controllers and Exchange Message Stores and attempts to restrict access through firewall filtering are likely to break the communications required for a CAS server to operate correctly. Microsoft suggests using Network Address Translation to direct HTTP/HTTPS traffic to the CAS server that is in the private network, although Microsoft also states that reverse proxy servers may be placed in the DMZ.
Microsoft states that the CAS server (running on Windows Server with the Exchange CAS Role) has been sufficiently hardened that opening it directly to HTTP/HTTPS access is safe. Perhaps this is true, but Microsoft also has a long history of security issues associated with IIS. Coupled with the requirement that the server is joined to an Active Directory Domain, there are concerns despite Microsoft's assurances to the contrary.
There are several options available, such as a proprietary firewall reverse proxy, IIS reverse proxy (optionally in a load-balanced server farm) and Apache (optionally in a load-balanced server farm). The Microsoft IIS option does not require joining the web servers to the domain, which enhances security. However, Apache is an entirely different architecture, which provides even greater security benefits.
The Test Environment
As depicted above, the external interface(s) of the firewall will permit HTTP/HTTPS traffic and Network Address Translate (NAT) it to an interface on a Linux server running Apache Proxy. Apache is configured to rewrite the requests to the CAS server https://exchange02.mydomain.com directories /owa, /ecp and /Microsoft-Server-ActiveSync. The CAS server then sues Active Directory to authenticate and access Mail Store and Hub Transport servers.The Apache Configuration
The following lines configure Apache to reverse proxy requests from the firewall server (cou-firewall.mydomain.com) to the Exchange CAS server (exchange02.mydomain.com). Under Debian Wheezy, these are placed in the /etc/apache2/sites-available/default file.<VirtualHost *:80>
ServerName cou-firewall.mydomain.com
ServerAlias exchangemail.mydomain.com
ServerAlias mail.mydomain.com
ServerAdmin webmaster@mydomain.com
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
Header always set X-Frame-Options SAMEORIGIN
Header set Server Apache
Header unset X-AspNet-Version
Header unset X-OWA-Version
Header unset X-Powered-By
ProxyRequests Off
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^/owa(.*) https://exchange02.mydomain.com/owa$1 [R,L]
RewriteRule ^/ecp(.*) https://exchange02.mydomain.com/ecp$1 [R,L]
RewriteRule ^/Microsoft-Server-ActiveSync(.*) https://exchange02.mydomain.com/Microsoft-Server-ActiveSync
DocumentRoot /var/www
<Directory />
Order deny,allow
Deny from all
</Directory>
<Directory /var/www>
DirectoryIndex index.php index.html
Options -Indexes +FollowSymLinks
Order allow,deny
Allow from all
</Directory>
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
</VirtualHost>
### SSL Host ###
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName exchangemail.mydomain.com
ServerAdmin webmaster@mydomain.com
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
Header always set X-Frame-Options SAMEORIGIN
Header set Server Apache
Header unset X-AspNet-Version
Header unset X-OWA-Version
Header unset X-Powered-By
ProxyRequests Off
ProxyPreserveHost On
SSLProxyEngine On
# owa
ProxyPass /owa https://exchange02.mydomain.com/owa
ProxyPassReverse /owa https://exchange02.mydomain.com/owa
# ecp
ProxyPass /ecp https://exchange02.mydomain.com/ecp
ProxyPassReverse /ecp https://exchange02.mydomain.com/ecp
# Microsoft-Server-ActiveSync
ProxyPass /Microsoft-Server-ActiveSync https://exchange02.mydomain.com/Microsoft-Server-ActiveSync
ProxyPassReverse /Microsoft-Server-ActiveSync https://exchange02.mydomain.com/Microsoft-Server-ActiveSync
DocumentRoot /var/www
<Directory />
Order deny,allow
Deny from all
</Directory>
<Directory /var/www>
DirectoryIndex index.php index.html
Options -Indexes +FollowSymLinks
Order allow,deny
Allow from all
</Directory>
<Proxy *>
SetEnv proxy-nokeepalive 1
SetEnv force-proxy-request-1.0 1
Order deny,allow
Allow from all
</Proxy>
SSLEngine on
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key
</VirtualHost>
</IfModule>
Note that the SSLCertificateFile and SSLCertificateKeyFile use the sss-cert-snakeoil files that are installed by default. These may be replaced with valid SSL files and referenced as such.
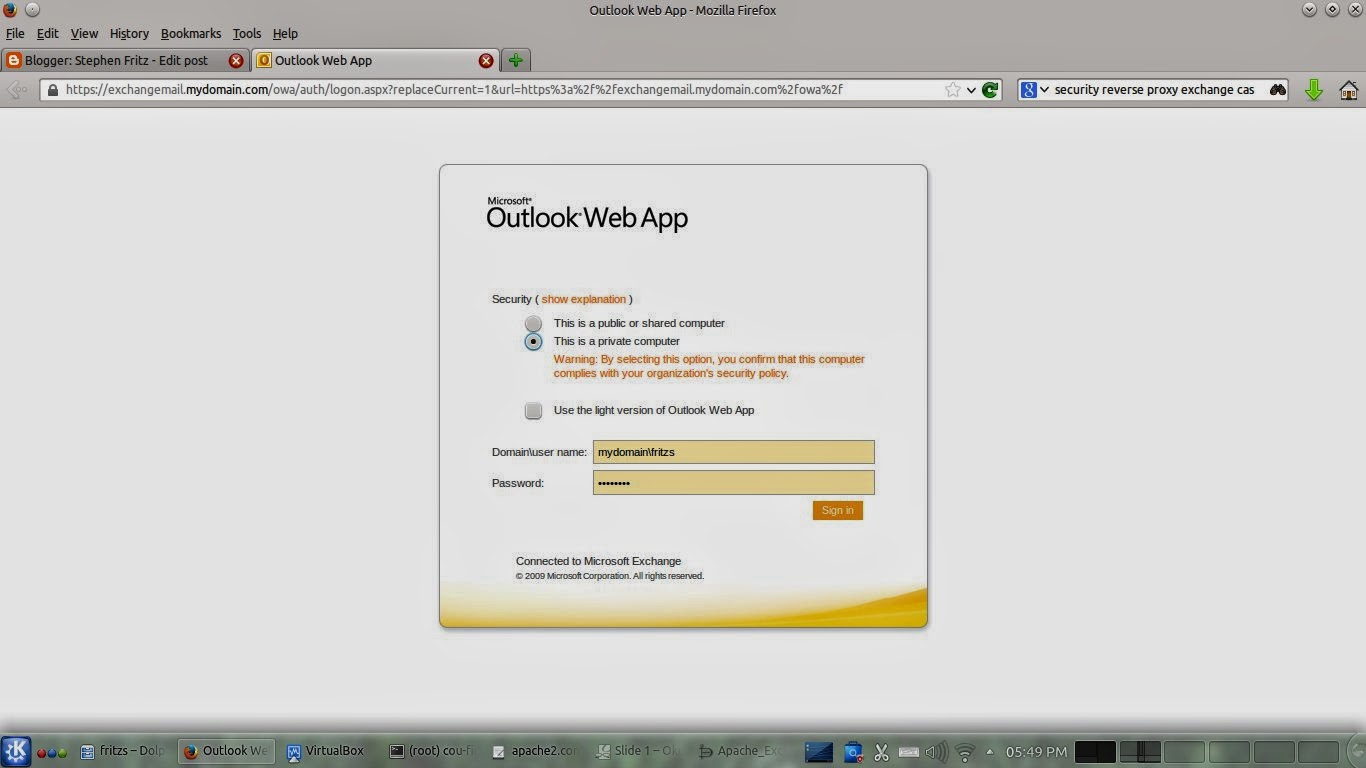
Reverse Proxy OWA
The SSL Certificate used for this example will not be verified, so the browser will present a warning when the web site is first accessed. This may safely be accepted.
After which, access to OWA is granted.



No comments :
Post a Comment